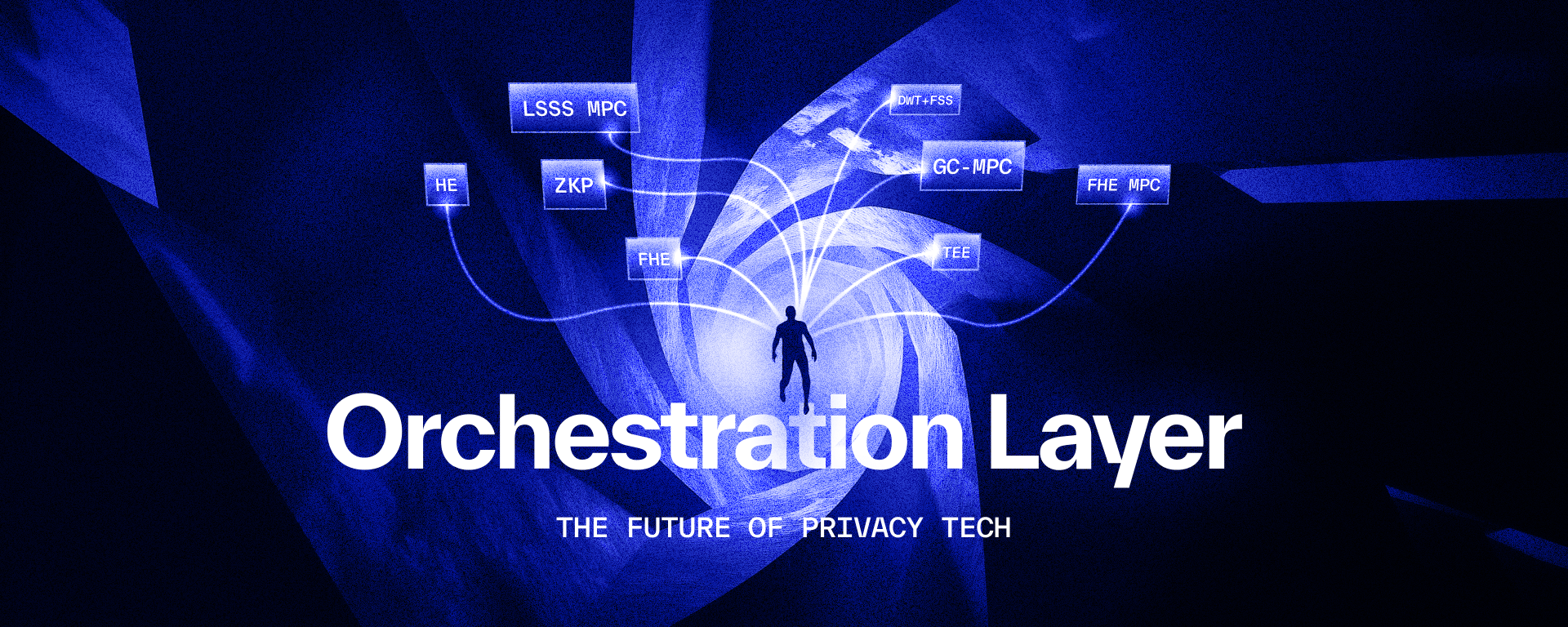
At the heart of Nillion’s design ethos for what a privacy-enhanced future looks like is the Orchestration Layer – a collaborative technical vision built upon the assumption that there is no single silver bullet primitive in cryptography that will be the right tool for every job. Different PETs, such as the different flavors of ???? Multiparty Computation (MPC), ???????? Fully Homomorphic Encryption (FHE), and ???? Zero Knowledge Proofs (ZKPs), are meant to solve different use cases. They also exist in a tradeoff space of many factors like performance, cost, maturity, and functionality. This tradeoff space is dynamic and completely dependent on individual progress in any of these fields. Each technology has its own unique properties and things get interesting when you combine them together.
You can think of the Orchestration Layer as a maestro, conducting its orchestra of cryptographic techniques together to perform more and more complex pieces. It’s a flexible approach that acknowledges that research doesn’t stop while infrastructure is being built and that bets on the value of innovation in the rapidly advancing research field of PETs. Though the orchestra may start small, each new instrument adds to what’s possible.
But what is the Orchestration Layer in relation to Nillion? There are two important pieces that make orchestration possible in Nillion: the Blind Modules and the SDKs. Nillion’s Blind Modules are the cornerstone technologies that power the Blind Computer – from nilDB delivering distributed, encrypted databases to nilAI offering private LLM inference and services for agents.
Levels of Orchestration
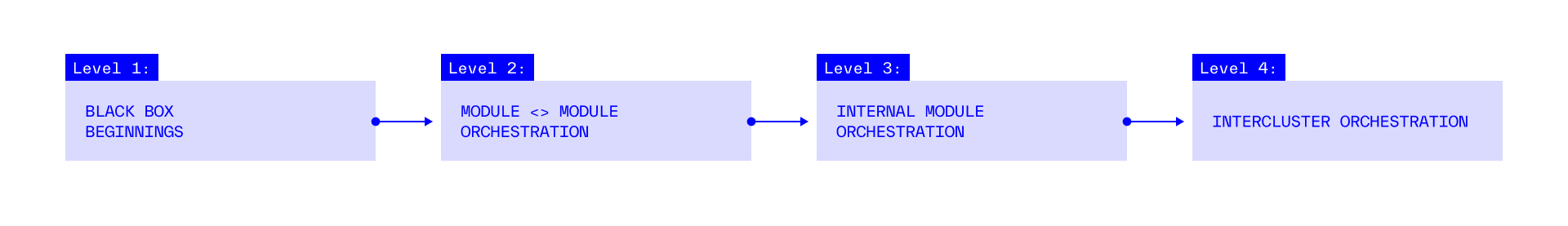
The idea of an Orchestration Layer that enables developers to easily create applications capable of securely storing and working with private data, while harnessing the power of various PET protocols, can exist at different levels of abstraction.
Level 1: Black Box Beginnings
Initially, each PET protocol operates in isolation within its own Blind Module. This stage sets the foundation, allowing for interesting combinations of PET protocols through manual orchestration between different Blind Modules. However, there are no built-in unified interfaces or abstractions beyond what occurs on the client side.
Level 2: Module <> Module Orchestration
In this phase, different Blind Modules are combined within each SDK, offering developers a simple, transparent, optimized, and unified way to work with multiple PET protocols without requiring any cryptographic knowledge. While the Blind Modules are not yet internally optimized because they only use a single PET protocol, a seamless, out-of-the-box combination of PET protocols is already available.
Level 3: Internal Module Orchestration
As Blind Modules advance and mature, different PET protocols are implemented within a Blind Module to offer developers the ability to find the desired point within the performance vs. security tradeoff space. Additionally, tailor-made protocols may be included to increase performance, security, or functionality. This added complexity is once again hidden from the developer, so no cryptographic knowledge is required.
Level 4: InterCluster Orchestration
Blind Modules operate on loosely independent networks, known as Clusters, which are coordinated by the NilChain. As the Nillion Blind Computer evolves, the same Blind Module can be implemented across multiple Clusters, each with a unique configuration. These configurations vary based on factors such as the number of nodes, their locations, reputations, hardware specifications, security threshold parameters, and more. This flexibility allows developers to leverage the same functionality across different Cluster setups, tailoring solutions to meet specific requirements for security, cost, hardware, regulatory compliance, and other needs
Today at Nillion: Road to Orchestration

Currently, the Orchestration Layer’s blueprint is in process of being realized across Nillion’s Blind Computer, its Blind Modules and SDKs, with steps of all four levels of the final vision in action.
One current example of a Level 2 implementation is the Secret Agent SDK, which combines the NilDB and NilAI Blind Modules. An example of a Level 3 implementation is the NilDB Blind Module, which supports both a linear secret sharing and a homomorphic encryption scheme. A near-term example is the NilAI Blind Module, which will combine a standard MPC protocol with a specialized protocol developed by Nillion that accelerates the secure evaluation of activation functions in an AI model.
For the Orchestration Layer to truly achieve its vision it must reach across the silos of cryptographic research that exist across academia, web2, and web3. Our vision is the creation of an incentivized collective system that breaks down these silos and rapidly accelerates innovation in the service of humanity.
Follow @BuildOnNillion on X/Twitter for more updates like these