We Are Living in a Data Crisis
Every day, billions of records move through systems never designed to protect them.
In 2024 alone, over 35 billion records were exposed globally.
Healthcare files, financial transactions, even private communications.
All compromised, often without users ever knowing.
And organizations paid the price: an average of $4.88 million per breach. But that’s not the true cost.
The true cost is trust that’s lost, and difficult to earn back.
The conversation around privacy has shifted. It’s no longer about ‘whether’ companies should act, it’s about how fast they do.
Enterprises across the globe are stepping up. They’re not just asking for change.
They’re building it.
Nillion is enabling that shift with a new foundation for data privacy: Blind Computation. At the heart of this foundation is a new kind of network, built to break the transparent glass and create a more private world.
Blind Computation: Privacy as Infrastructure
The internet was never designed for private collaboration.
Every time data is shared or processed, it’s exposed to the platform, the operating team, and the infrastructure underneath.
Blind computation changes that.
At the center of Nillion’s Blind Compute is the PetNet: A decentralized, privacy-first network where encrypted collaboration becomes possible, where computation happens without exposure, and privacy is protected by architecture.
Blind computation on the PetNet turns sensitive information into a usable asset, without ever making it vulnerable.
It introduces a new method where sensitive data never needs to be decrypted to be useful. Instead, it’s split into encrypted fragments and securely distributed across a network of nodes called nilDB. When computation is needed, the data is reconstructed and processed inside a Trusted Execution Environment (TEE) called nilCC, using a model chosen by the user. At no point is the data exposed in plaintext outside the enclave, ensuring complete end-to-end privacy.
Blind computation solves the privacy problem, but to scale it, to run meaningful workloads, handle high value data, and operate across industries, it needs another layer: trust!
Not trust in the sense of blind faith.
But verifiable trust in who’s operating the network. In decentralized systems, the weakest link isn’t just technical, it’s human.
If the operators running critical infrastructure lack credibility or accountability, the entire promise of privacy breaks down.
That’s why the PetNet is more than a technical achievement, it’s a trust framework.
Its architecture is powered by a distributed network of nodes, and who runs those nodes matters the most. Because while no node ever sees full data, the integrity of the network depends on how reliably, transparently, and independently each one functions.
This is where the Enterprise Cluster comes in.
Nillion has partnered with some of the world’s most recognized enterprises to run nodes on the PetNet:
- stc Bahrain
- Cloudician by Alibaba Cloud
- Pairpoint by Vodafone
- Deutsche Telekom
…with another leading global enterprise to be revealed soon.
These enterprises are more than symbolic alliances, these are entities that serve hundreds of millions of users daily.
They bring operational rigor, global infrastructure, and established reputations into the privacy fabric of the PetNet and by running nodes, they’re not just validating the network, they’re powering it.
This early participation paves the way for broader enterprise adoption of privacy-preserving infrastructure.
It’s the first step in a longer journey: one where these organizations build, test, and eventually deploy new products directly on the PetNet.
More than Validation, It’s a Strategic Step
Operating a node on the PetNet isn’t just about supporting the network, it’s about shaping the future.
Some of these enterprises are learning by doing. They’re exploring how privacy-enhancing technologies can integrate into their own systems. They’re building confidence in infrastructure that’s ready for scale.
And they’re setting the stage for privacy-first products, services, and standards.
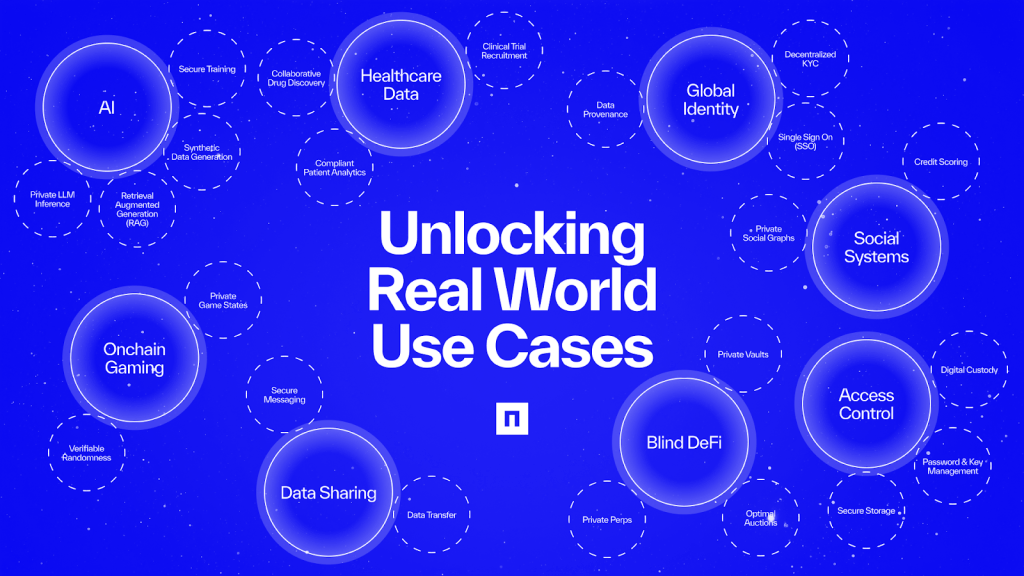
Real Privacy, Real Use Cases
When enterprises run blind compute nodes, the applications aren’t theoretical. This partnership is a significant step in igniting real world use cases where applications are built with privacy at their core.
- Telecom: Analyze network data securely, without exposing user behavior.
- Finance: Perform risk modeling and fraud detection on encrypted data.
- Healthcare: Collaborate on sensitive research without transferring or revealing personal information.
These applications don’t require trust. They’re built on it.
Modularity for the Real World
The Enterprise Privacy Cluster is designed for adaptability.
Developers can configure networks with enterprise-grade operators, self-hosted infrastructure, or web3 community nodes. They can tailor security thresholds to meet the demands of compliance, jurisdiction, and performance.
Laying the Foundation for What Comes Next
This is the beginning of something bigger.
It’s the start of a privacy network grounded in real-world credibility, built for practical use, and modular by design.
This is how Nillion turns blind computation from theory into infrastructure.
And how a network built on privacy becomes the default substrate for the next internet.
The internet for intelligence.




